From Casual Networking to Crypto Theft: My $187K Lesson
The Spectra Job Interview Scam
In the expansive and ever-evolving digital landscape, our quest for new opportunities can sometimes lead us into the murky waters of deceit. This is a tale of intrigue, digital trust, and the unforeseen dangers lurking within the professional world. My public background in data science and crypto development enhanced the ability of a sophisticated team of Russian nationals to steal ~$187k in funds from me in a matter of just a few hours.
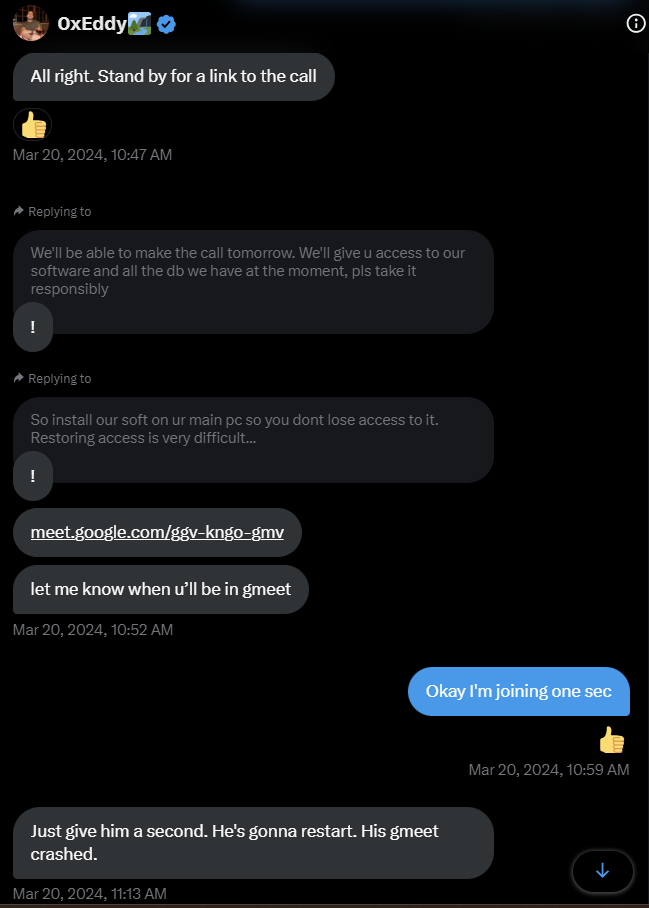
On March 18, 2024, my digital odyssey began with an innocuous Twitter message from a person identifying as Associate 1 (0xEdddy). Our conversations, initiated under the guise of casual networking, swiftly pivoted to a discussion about a potential job role tailored to my expertise in data science. The company in question, Spectra Chat, appeared to be a legitimate enterprise at first glance, prompting me to share my resume with enthusiasm and hope.
What followed was a series of communications with another supposed employee in the organization, Associate 2 (JiangWeb3), culminating in an elusive Zoom interview that never materialized despite my persistent efforts. This did seem a bit odd at the time but didn’t raise any immediate red flags. In hindsight, the specific request to join from a computer should have been suspect.
The plot thickened the following day with a Google Meet interview Associate 1 (0xEddy) arranged for me to meet Associate 3 (DJ_kubaking), who represented the supposed HR face of Spectra Chat.
This 30-minute interview, filled with standard queries, seemed to solidify the authenticity of the opportunity. However, this narrative took a dark turn when I was asked to install the Spectra Chat software, an action that would unwittingly become the catalyst for my nightmare scenario. Following the Spectra Chat installation, my MetaMask wallet was compromised, leading to the unauthorized transfer of funds and the loss of highly valuable NFTs.
This experience, though harrowing, serves as a cautionary tale about the perils of digital engagement and the importance of vigilance in an era where online scams have become increasingly sophisticated.
Spectra Scam Company
When researching the company, the first thing I noticed was their rather impressive landing page. I have to give props to the designer as the clean dynamic pages with animations seemed to be very professional.
When I dug further, I realized that the Spectra Team had simply stolen the webpage of a legitimate web3 app called Status, tweaking the logo slightly by using a darker black-green color rather than the gradient of blue/purple/orange that the legitimate company uses. Status app works as Ethereum L2 solution to reduce gas fees and seems to be working on a hardware wallet as well.
The hardware wallet was the reason I was able to find the original Status company, as the fake page which Spectra cloned links to a Keycard page on a Status webpage.
The legitimate Status.app website that had its design entirely stolen and cloned by Spectra.
Going on the offensive
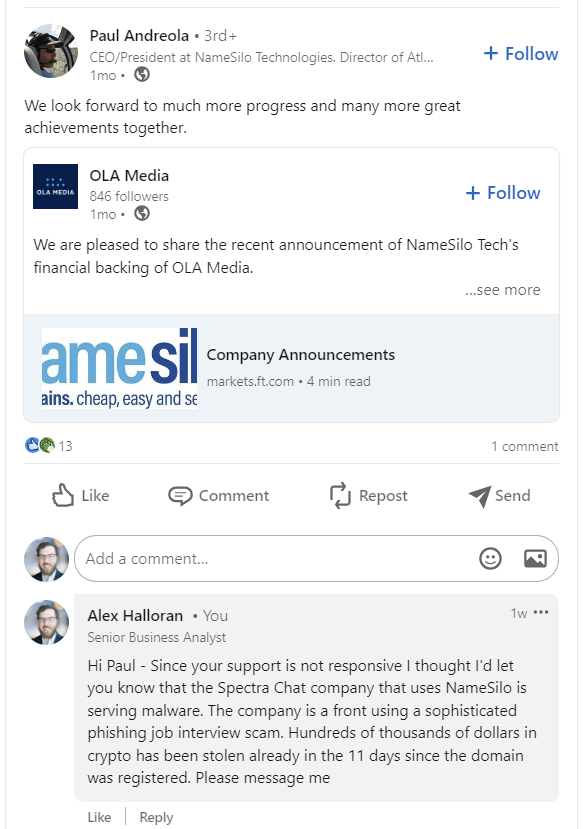
In an attempt to prevent others from falling victim to the attack, I reported their original domain name (spectra.chat) to their Registrar, NameSilo. NameSilo was not initially responsive to my ticket, but after some pestering on social media they responded (Fun Fact: comments on LinkedIn can’t be taken down, so if you ever need to pester a company…this is the place to do it). Here’s me commenting on the posts from the CEO of NameSilo, Paul Andreola.
After about 4 hours of investigation, NameSilo took the domain down.
This stopped Spectra from having a dedicated site to download their app, with the contained malware, for a couple of days. The Spectra Team then registered under the domain spectra.social and changed the X handle to @SocialSpectra from @SpectraChat.
Spectra is still active at a new domain spectra.social which appears to be registered to a shady registrar in Hong Kong, notorious for ignoring takedown requests for active scams. I’ve submitted abuse notices, but cannot seem to get traction from the company.
Malware and Technical Aspects
Thanks to Sero for providing a detailed investigation on the security aspects of the software in his own post, I was able to understand the functionality of the malware.
The SpectraChat/SpectraSocial malware, delivered via a deceptive .exe installer, infiltrates local machines by installing a folder of C++ files and ensuring its persistence by copying and renaming itself into random folders. This action, coupled with a misleading error message about missing "C++ Drivers," can prompt victims to contact the hackers, further entangling them in the scam. At the time since they mentioned the software was in beta, I didn’t think much of a simple error message.
Notably, this malware exploits a gap in Windows Defender's protection by masquerading as an installer, rather than the malware itself. Once operational, it hijacks the victim's browser to manipulate crypto wallet plugins, enabling remote control or the automated transfer and sale of the victim's digital assets. A particularly insidious feature is its ability to hijack the browser's copy/paste function, replacing copied wallet addresses with the scammer's address, thus thwarting any attempts by the victim to safeguard remaining assets. Despite its sophisticated mechanisms for browser and financial manipulation, the malware does not appear to extend its reach to control the entire host device, escape from virtual machines, or infect the network, as experiments with untouched seed phrases and network monitoring have shown.
Since Associate #3 had friended me on Discord, I believe they watched my online status to appear “Away” before finally moving funds out of my metamask wallet as it occurred during a brief moment away from the laptop while I was showering.
Potential Obladaet Connection
The interviewer I spoke with on Google Meet, Associate 3 (DJ_kubaking), had a linked X profile featuring branding from a Russian rapper by the name of Obladaet (Nazar Votyakov). related to the rapper’s merch/lifestyle brand of “Player’s Club”.
The link on the X dj.kubaking profile then led me to an instagram profile for @playerslub.studio featuring pictures of a Russian rapper named Obadaet (Nazar Votyakov) and his entourage. Pay attention to the Player’s Club logo that Obladaet uses, including the specific pink-purple color scheme as this is relevant for other connections to him.
The playersclub.studio profile links to a separate instagram page with the handle @kennyp7ayer, an apparent reference to Obladaet’s song released 11/23/2017 by the same title.
I found a post on X about attempts in 2023 by the @kennyp7ayer account reaching out to artists in an attempt to install malware on their computers. Original tweet thread.
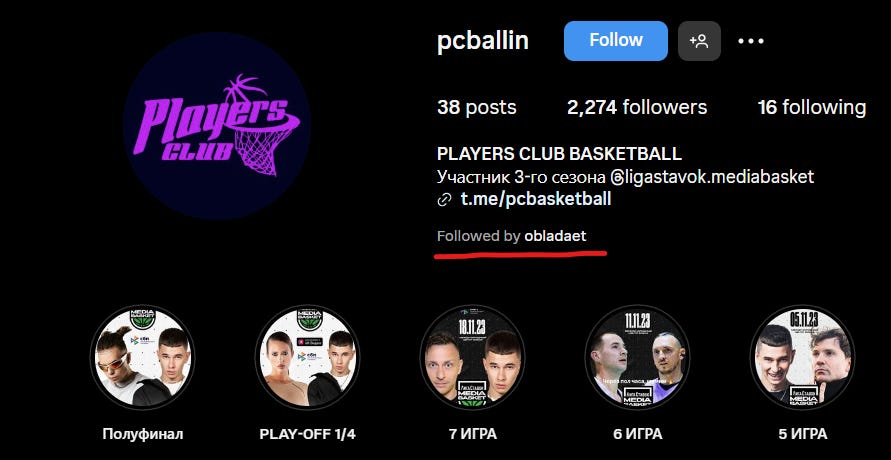
The main @obladaet instagram profile features a link in the bio for the basketball team @pcballin, using the same pink-purple color scheme with the @playersclub.studio profile.
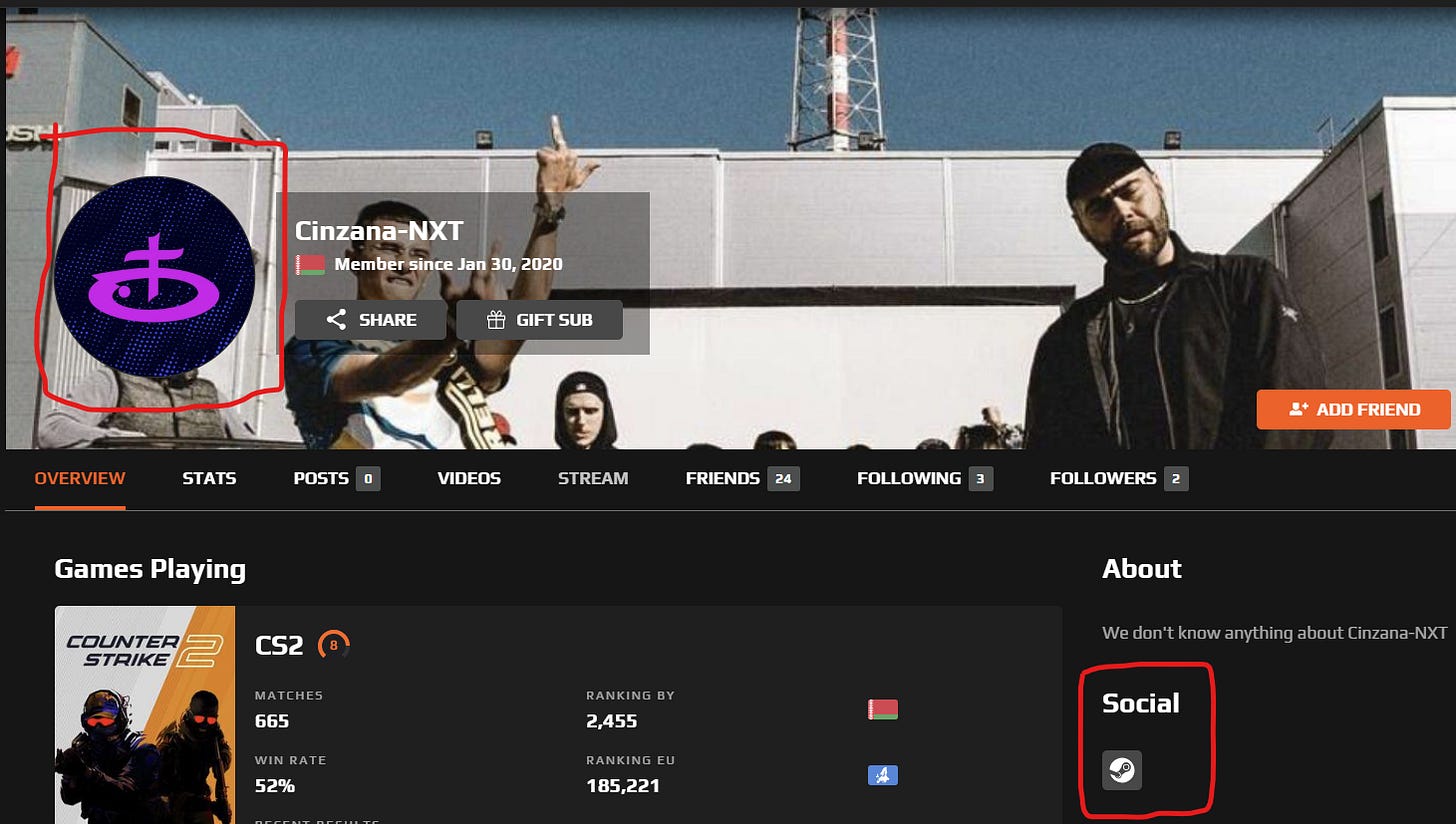
Image searches for the specific pink-purple version of the players club logo only show on a gaming website for the handle Cinzana NXT, which appears to be an active CSGO player. On the left side of the banner image with the middle finger up, is Obladaet.
The Face-It page links to their corresponding Cinzana Steam profile.
When looking through Cinzana’s Steam friends list I noticed a profile for a friend of Obladeat by the name of Mark Bulah (MARKBULAHH) known for his Youtube prank videos.
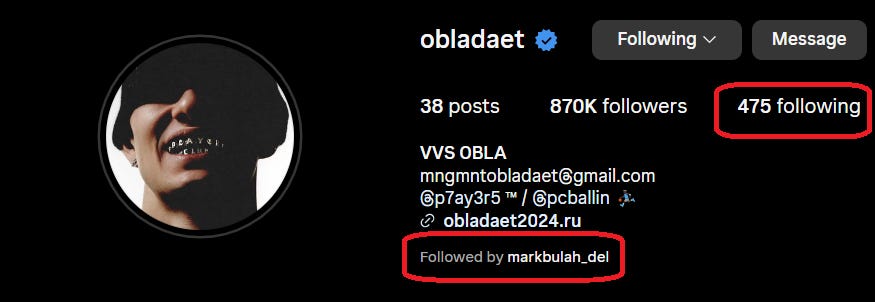
Looking at Mark Bulah’s Steam Page, I saw a link for his instagram profile.
Examining Mark’s instagram profile, I see that he is reciprocally followed by Obladaet. This is especially notable when you see how few people each of them follow in total, particularly for Mark Bulah following less than 100 people while boasting 759k+ followers.
Obladaet the rapper, himself, appears to be a crypto native with lyrics from the song Mutant translating from Russian into “crypto in my wallet:”
In the chorus of the same “Mutant” song appear lyrics about NFTs and scams. Could this just be coincidence? Or is it another case of a rapper self-incriminating through bragging?
The “green elixir” in the rest of the lyrics refers to the process where Bored Ape Yacht Club NFT owners could consume either the M1 or M2 mutant serum to create a mutant form of their original NFT ape.
The Kenny name used on the instagram profile linked to Associate 3 also appears in lyrics from his song BAME with another brag about theft.
Obladaet’s song “David Beckham” makes a reference to being a scammer, along with a nod to his blue Lamborghini.
Speaking of his Blue Lamborghini, the most recent registration for the plate SN17 AEY appears to be in the London area. Obladaet seems to spend large amounts of time in both the UK and Russia, consistent with chat references to Associate 2 also being in London.
Blue Lamborghini Photos with Obladaet in London.
Obladaet has had a heavy instagram presence for years growing his main account to 800k followers along with a merch profile using the instagram handle p7ay3r5. Looking through comments on posts from the merch account shows many claims of fraud due to people not receiving the merch orders made.
Typically with merch purchases, you would see fans of the artist tagging the merch brand or the leading artist related to the clothing, but I’ve been unable to find any regular people wearing the Players Club brand. All photos thus far point only to Obladaet and common members of his entourage wearing the brand.
Obladaet is no stranger to the fashion industry, with his own dedicated profile highlighting every piece of an outfit including pricepoints. This account first posted back in August of 2020. How does a C-list Russia in rapper afford so much designer clothing?
I dug further after seeing the playersclub.zone domain linked in several Obladaet associated profiles. Obladaet’s most recent YouTube music video on 3/8/24 contains a link to the playersclub.zone domain at the bottom of the video description, the same one linked in various alternative profiles on instagram. Why promote a merch website where you’re unable to actually buy merch?
I was unable to determine if playersclub.zone domain is a real merch website or not as access is blocked by an email form. I tested the website form with temporary emails, but never received a message from the site…
WhoIs registration for the supposed Players club merch site shows it was registered through the registrar reg.ru
A quick search of the register abuse phone number from the WHOIS record shows a number of related scams, some of which follow the common theme of gaming and merchandise sales fraud.
Obladaet Token?
I found a relatively new crypto token made this month with the Obladaet name. Suspciously, there are only two transactions on record for the token. Why would someone create a token and then lock 90% of the issued token in the liquidity pool with a closed source, unverified contract?
The contract address for the token shows its creation on the BASE network (a second layer on the Ethereum network) on 3/22/24, just 2 days after the theft from my metamask wallet. I tried my best to see if I could link the hacker wallet funds to the creation of this contract, but it was too many transactions to find anything definitive when examining with chainanalysis.
When searching for info about “Players Club Studio”, I found an odd forum post advertising production services for $50k. The post was made 1/19/23, and is the only post from the profile, which again uses the same Players Club logo and references the Kenny alias of Obladaet.
Tracing the stolen funds
Due to the public nature of a transparent ledger in cryptocurrency, I was able to track the flow of funds from an initial hacker wallet destination to other secondary wallets, a portion of which was sent to the Kucoin exchange.. Etherscan allows you to see all of the outgoing transfers from my wallet. The split of 50%, 25%, and 25% in secondary transfers from Hacker Wallet 1 would seem to indicate several cuts to the team involved (2 people bringing in leads, 1 executing the attack?)
Here are the hashes of the major transfers that occurred, linked to Etherscan:
0xc0f4fcee0f4440e0ee89f6f81ddd7389ec8232616f7f771eef3f4bf663540f20
14 ETH ($49k)
0xb348efc797805b65ab989fa6e90ed3316c63f1170f1dee67d3c39e88d62a8fb7
0.8 ETH ($2.8k)
0x18405edd01a66d1a7aa476fa8a344dc6ab890f65586fb978fb7e5b53ef865e93
39k USDC ($39k)
0xce678f05475ee7420d6fa78b8d4b99bf33fb53e1d2f186d8fa0802df06da0f74
27k LENDS ($2.8k)
0x9cea18637bbd71733031d66a0ff78978d1aa2c3a52b111e20e5b863fb3389dd0
90 GNUS ($11k)
0xc9fc57fd51cc2a37b835939b8bc0c2a09c124deefd14af529490ca159a4b5fc8
709k M87 ($5.7k)
0x4192edf4fcd209384d1e715beda0c90dee9da3a0a1638b2117ff8bdb3084cbbc
963k ZYN ($73k)
Diagram of the transfers to main hacker wallet and subsequent flows, totalling $187k.
I was able to see funds in Hacker Wallet 4 moving to the Kucoin exchange. The amount of funds transferred to Kucoin were larger than originally stolen from my wallet which may indicate funds stolen from other victims. I contacted Kucoin, but they were unable to assist with any freezing of accounts without a court order. It’s likely that by the time I receive a court order, the funds will have already been moved off the exchange.
Below are transactions from Hacker Wallet #4 with transactions outlined in Red as my funds, while the blue transactions more recently on 3/26 appear to be from another victim, currently unknown.
Several of the NFTs in my wallet during the attack were sold by accepting existing, outstanding Opensea offers. Most of the NFTs in my wallet were well-known collectibles with a corresponding high liquidity. As a long-time follower of Jack Butcher, I had been lucky to be part of his release of the Checks project and Opepens. I had 6 Opepen NFTs, a dynamic profile picture project where artists submit their proposed work to be included in future sets. At the time of writing this blog post, the Opepen collection was ranked #4 on Opensea.
My most valuable Opepen #15168 was “revealed” at the time of the theft, from a set that was created in collaboration with Pudgy Penguins, one of the most well-known NFT collections with Pudgy Penguin toys appearing in mainstream stores like Walmart. The current price for the NFT is listed as 2.7 ETH ($10k), but was sold to this collector (Hot-MILF) at a price of 1.51 ETH ($5.5k).
I believe it’s safe to assume that the NFT buyers were not malicious in their purchases as the sales occurred around market rates and some of the users had sent me previous offers for the same NFTs in question well before their unauthorized sale on 3/20/24.
Other Victims and Warnings
I have been active on X since the attack, monitoring for others who had fallen victim, and warning others who mentioned the company. I was able to find a handful of other known victims.
Link to Naved’s original tweet thread
Another victim of Spectra
George’s original Tweet warning others. I am unsure if he fell victim or not.
I spoke with RationalRao privately who nearly fell victim to the attack, but appropriately questioned the need to install an application. His tweet thread
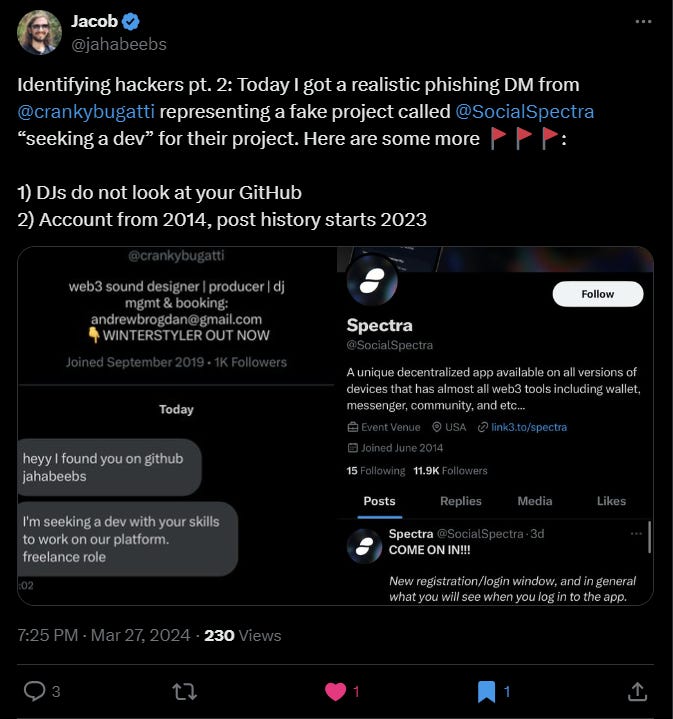
Jacob on X posted a good thread analyzing the approach of Spectra.
Lessons Learned
Due diligence is important. I should have researched the company more than I had prior to the interview and in hindsight they moved much more quickly between first contact and interview
Vulnerability of Hot Wallets. I have kept a large portion of my crypto holdings on hardware wallets in the past. In the matter of 6 months through some amount of sheer luck, I ran my metamask wallet from $10k to nearly $300k in total holdings. I was actively cashing things out just prior to the attack and luckily moved a large chunk days prior to theft of the remaining holdings. A majority of the price appreciation was due to sheer luck as I designed the logo for the Zyncoin project in exchange for some payment in early tokens and bought some additional exposure after the fact.
This is a common scam. I was amazed at the sheer volume of others who have encountered shady individuals posing as companies or fallen victim to the scam Her is an article about a developer being targeted from LinkedIn and a tweet from a crypto founder.
Conclusion
I hope this article brings some additional awareness to this type of attack. This ordeal has been a painful lesson for me that I was unprepared to receive. I’m hopeful that the FBI is able to assist me, especially due to the large amount of funds stolen, but am pessimistic thus far given the lack of response from my claim. While filling out a report, I realized how woefully unequipped our government is to handle this new type of crime. Please share this article if you have friends or family that use crypto.
Should you have additional information about the criminal organization, or are a victim yourself, please leave a comment below to assist myself and others pursuing the individuals involved.
Subscribe to Alex’s newsletter by clicking the button below for future updates